When I applied to Walden University, there were some choices that I needed make in regards to which program I would enroll in. I relied on my past experience and some of my current goals to direct me to the Bachelor of Science degree in Computer Information Systems (BSCIS) with a concentration in Information Systems Security (ISS), a process which truly motivates me. Revisiting my goals and lending them power to help navigate the world of academia, I needed to ensure that these goals still held true. The first assignment in the Introduction to Information Systems class afforded me the opportunity to do just that, while this assignment will allow me to review my goals once again.
My affinity towards positive social change (Schadone, 2009) is unwaivering, as is my desire to achieve a position in the field of disaster management. I do feel, however, that my chosen degree program is ill-prescribed to prepare me for such ambitions. Though there has been a great incentive to involve the engineering sciences into public policy administration (Connolly, 2009), my experience with the BSCIS degree, even with the ISS concentration, leads me to believe that the curriculum does not satisfy my current needs or goals. I do believe that a career in Information Systems Security would provide an opportunity to reach many of my goals, but other academic directions would provide a more solid foundation for me to build upon.
As of this writing, I have decided to research other avenues of academia which might be better suited to providing the core educational opportunities that would benefit me the most. I have decided that the B.S. in Health Studies with a concentration in Health Administration would be a better fit at this time. I hope to use this degree to propel me forward into an opportunity to earn an MPH with a concentration in Emergency Management and, ultimately, a Ph. D. in the same.
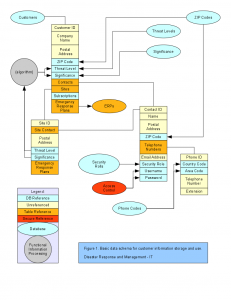
As the H1N1 influenza virus reminds us all about the 1918 “Spanish Flu,” there is an undertone of personal responsibility and preparedness in the event of a pandemic (Bornstein & Trapp, 2009), of which conditions are favorable. I plan to take personal responsibility in this and other potential disasters to position myself as an expert in the field helping to promote plans and policies to mitigate and respond effectively to such incidences. Though, I am versed in the computer sciences, I feel that my position as a health official would be better utilized in these times of crisis. Perhaps one day in the future I will return my focus on computing, but until then, my social conscience and sense of community seem to be my only defining factors.
Bornstein, J., & Trapp, J. (2009, June). Pandemic Preparedness: Ensuring Our Best Are Ready to Respond. IAEM Bulletin, 26(6), pp. 6, 14. Retrieved August 22, 2009, from http://www.iaem.com
Connolly, J. (2008, September). Bridging the gap between engineering and public policy: A closer look at the WISE program. Mechanical Advantage, 19. Retrieved August 22, 2009, from http://www.asme.org
Schadone, M. F. (2009). Information Systems and Me: My Professional and Career Goals. Minneapolis, MN: Walden University.